Ipsec
This five-step process is shown in Figure 1-15. Aber bei IPsec hat man es mit den Produkten unterschiedlicher Hersteller die trotz Standard untereinander nicht oder nur begrenzt kompatibel sind.
Presentation Du Framework Ipsec Cisco Goffinet Org
Weil IPsec eine lange Entwicklungszeit hinter sich hat gilt es als sehr sicher.

Ipsec. IPsec is often used to set up VPNs and it works by encrypting IP packets along with authenticating the source where the packets come from. IPsec provides a standards-based VPN implementation that is compatible with a wide range of clients for mobile connectivity and other firewalls and routers for site-to-site connectivity. Diese Ports benötigen Sie für IPSEC.
Ziel ist eine sichere Kommunikation über das potentiell unsichere IP-Netz wie beispielsweise dem Internet. A negotiation policy is specified as a policy provider context associated with the filter. Support for nested SAs is optional.
A LT2P IPSEC VPN can exchange either a pre-shared key. IPsec headers AHESP and cryptographic algorithms are specified at these layers. IPsec assumes only that outbound and inbound traffic that has passed through IPsec processing is forwarded in a fashion consistent with the context in which IPsec is implemented.
Die Funktion Smart Environment Detection merkt sich zuletzt genutzte Netzwerke samt aller. Insbesondere sollen die CIA-Schutzziele wie Vertraulichkeit durch Verschlüsselung Authentizität und Integrität durch. IPSec steht für die gebräuchliche Kurzform von Internet Protocol Security und ist eine Erweiterung des IP-Protokolls um Authentifizierung und Verschlüsselung.
Damit der sicheren Kommunikation nichts im Wege steht sollten alle Teilnehmer am IPSEC folgende Ports und Protokolle freigegeben haben. IPSec Authentication Header AH The protocol ensures a digital signature on each packet to protect your data and network. Discover Solutions for Factory Automation Workload Consolidation Smart Building More.
It helps keep data sent over public networks secure. The first machine a windows 2012 server will act as the VPN server. What is IPsec.
The protocols needed for secure key exchange and key management are defined in it. Je nachdem wie Sie IPSEC nutzen benötigen Sie unterschiedliche Ports und Protokolle. What are IPSEC Policies and how do I work with them.
IPsec offers numerous configuration options affecting the performance and security of IPsec connections. Determining what type of traffic is deemed interesting is part of formulating a security policy for use of a VPN. In this example we will set up IPSEC to encrypt communications between two windows machines.
The policy is then implemented in the configuration interface for each. IPSec-VPN-Client mit Unterstützung jeder IPSec-Firewall zum sicheren Einwählen in ein Netzwerk. IPsec gilt im Bereich VPN als der Standard an dem man nicht vorbei kommt.
IPsec vs SSL. The better performance depends on the hardware quality and technologies. The WFP API can be used to specify the Security Associations.
This means that the content cannot be altered without discovery. The second machine a Windows 10 client will act as the VPN client. IPsec is a group of protocols that are used together to set up encrypted connections between devices.
Within the term IPsec IP stands for Internet Protocol and sec for secure. It also allows the recipient to verify that the received packets were actually sent by the originator or not. Local vs Remote In this document.
There are roughly two parts to an IPsec implementation. If youve studied Windows 2000 security much then you know that one of the biggest security features thats included in. If required it requires coordination between forwarding tables and SPD entries to cause a packet to traverse the IPsec boundary more than once.
One kernel part which takes care of everything once the encryption or signing keys are known and one user-level program which negotiates beforehand to set the keys up and give them to the kernel part via an IPsec-specific kernel API. Die UDP-Ports 500 und 4500 sowie das IP-Protokoll ESP. The user-level program can also be configured to renegotiate keys periodically so no keys are used.
IPsec protocol sets up a tunnel that connects the client to the server through client software that may slow the performance because it takes time to initiate a connection but this isnt the case with IKEv2IPSec. It also defines the encrypted decrypted and authenticated packets. Figure 1-15 The Five Steps of IPSec.
IPSec tunnel terminationIPSec SAs terminate through deletion or by timing out. IPsec also includes protocols for establishing mutual authentication between agents at the beginning of the session and negotiation of cryptographic keys to be used during the. AH keeps you protected.
Vor allem auch deshalb weil die Sicherheit immer wieder verbessert wurde. Realistically for low to moderate bandwidth usage it matters little which options are chosen here as long as DES is not used and a strong pre-shared key is defined unless the traffic being protected is so valuable that an adversary with many millions of. IPSec relies on the following core protocols for encoding your information.
Ad Browse the Catalog for Innovative Solutions Developed by Intel Partners. The IP security IPSec is an Internet Engineering Task Force IETF standard suite of protocols between 2 communication points across the IP network that provide data authentication integrity and confidentiality. The keying module enumerates the policy provider contexts based on the traffic characteristics and obtains the policy to use for the security negotiation.
Internet Protocol Security IPsec is a protocol suite for securing Internet Protocol IP communications by authenticating and encrypting each IP packet of a communication session. It supports numerous third party devices and is being used in production with devices ranging from consumer grade Linksys routers all the way up to IBM. IPSEC utilizes IP Protocol 50 ESP IP Protocol 51 AH and UDP Port 500.
Exemple De Configuration D Un Tunnel Ipsec Lan A Lan Entre Deux Routeurs Cisco
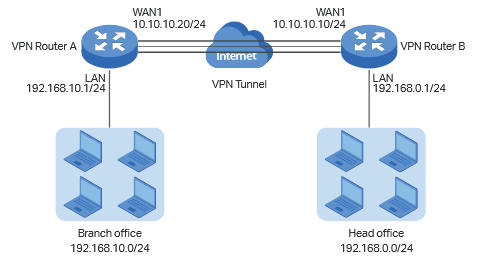
Comment Configurer Un Vpn Ipsec Lan A Lan Sur Un Routeur Tp Link A L Aide De La Nouvelle Interface
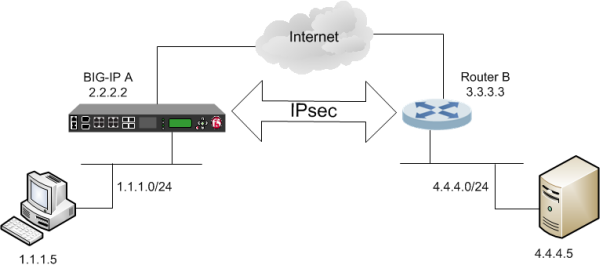
Askf5 Manual Chapter Configuring Ipsec Between A Big Ip System And A Third Party Device
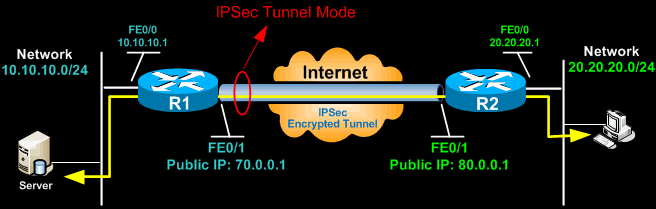
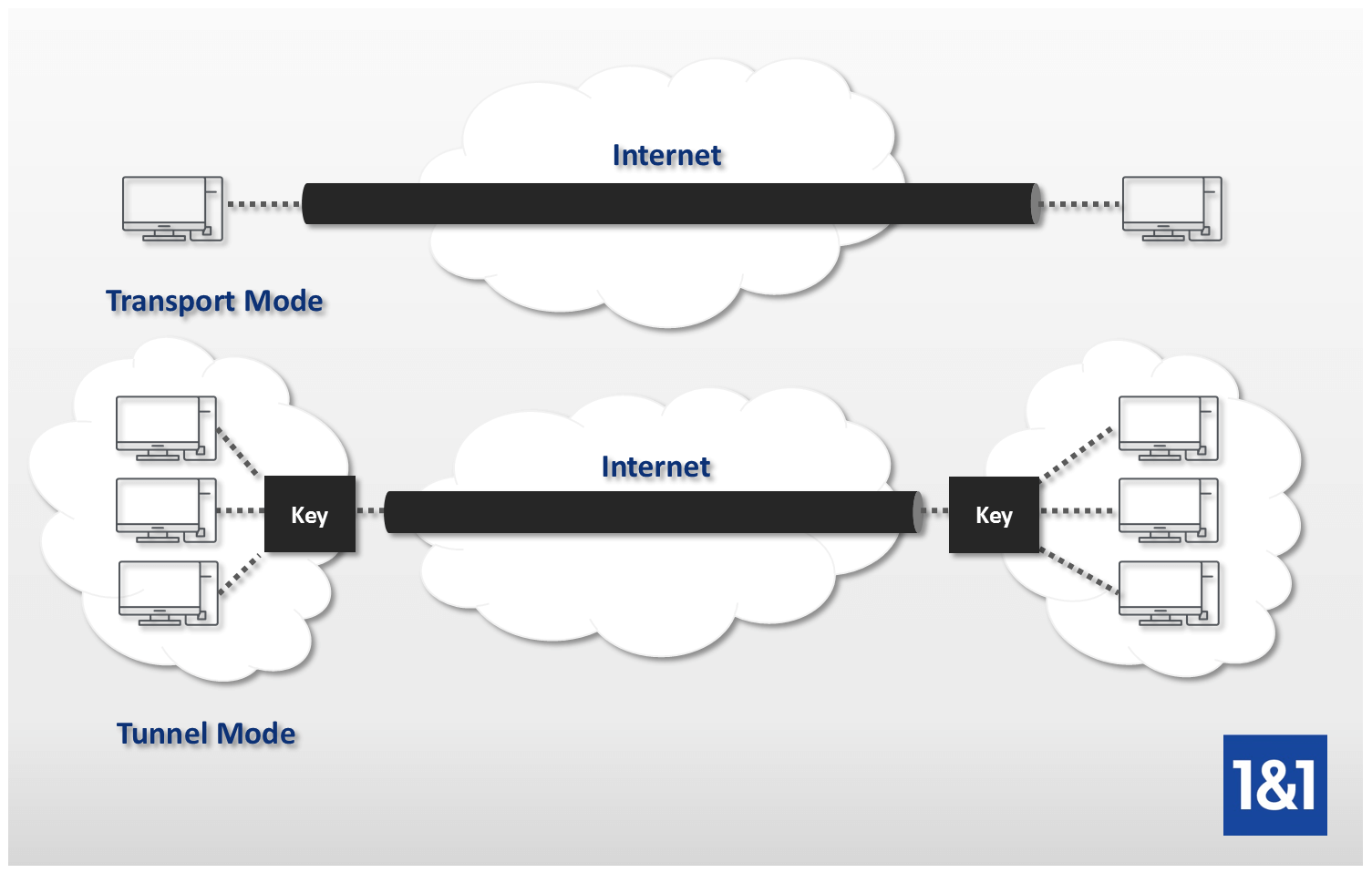
Understanding Vpn Ipsec Tunnel Mode And Ipsec Transport Mode What S The Difference

Portail Ipsec Vpn Serveur Rs232 Ethernet Perle
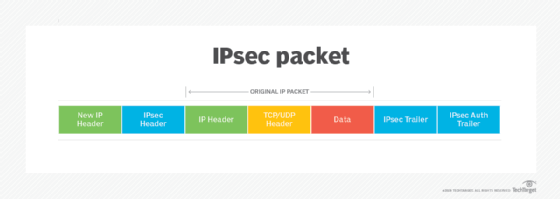
What Is Anti Replay Protocol And How Does It Work

Portail Ipsec Vpn Serveur Rs232 Ethernet Perle
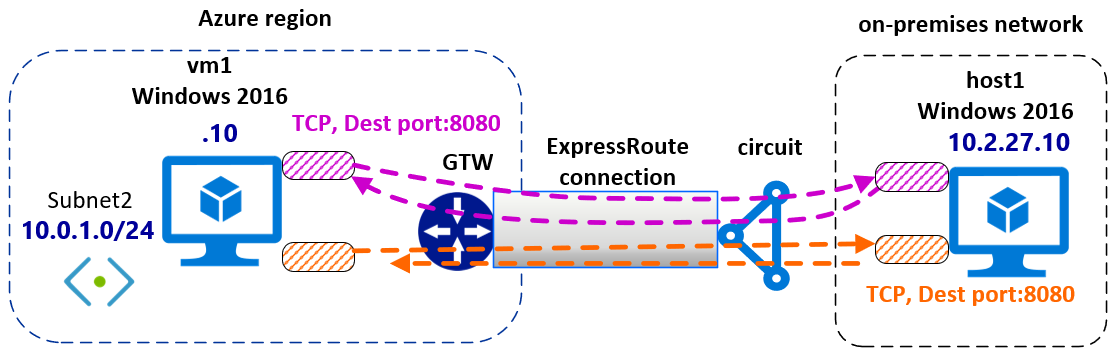
Peering Prive Azure Expressroute Configurer Le Mode De Transport Ipsec Hotes Windows Microsoft Docs
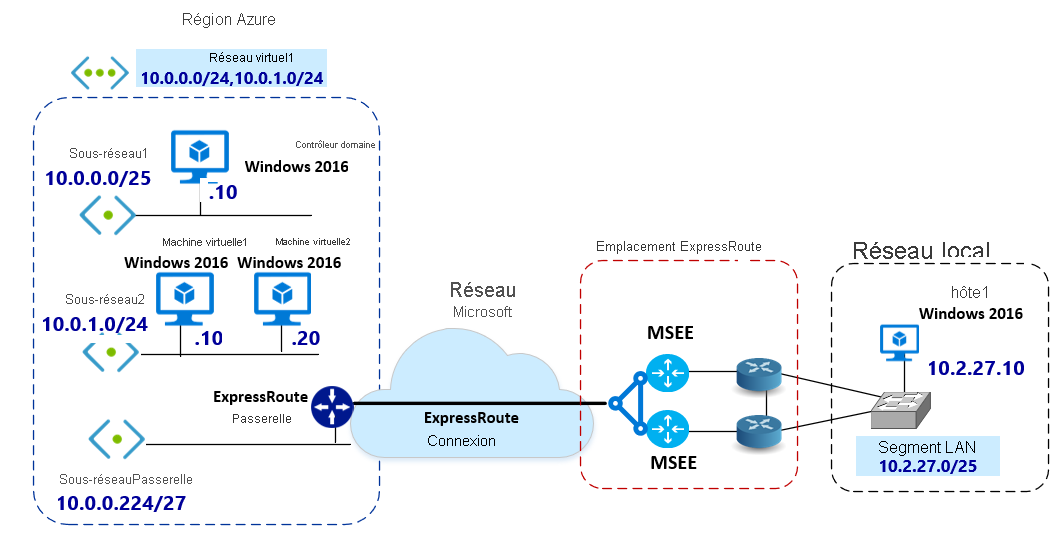
Peering Prive Azure Expressroute Configurer Le Mode De Transport Ipsec Hotes Windows Microsoft Docs
Ipsec Application In The L2vpn Or L3vpn Scenario Me60 V800r010c10spc500 Feature Description Security 01 Huawei

File Ipsec Vpn En Svg Wikimedia Commons
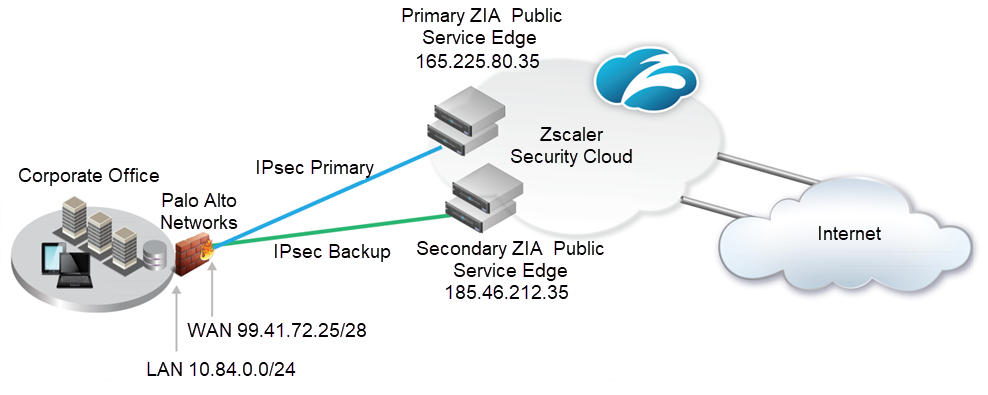
Ipsec Vpn Configuration Guide For Palo Alto Networks Firewall Zscaler

Ipsec Vpn Authentication By Certificate
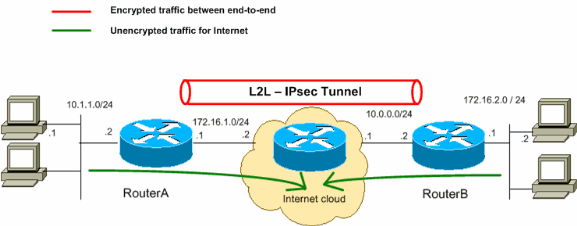
Configuration De Reseau A Reseau Via Ipsec

Ipsec Vpn Authentication By Pre Shared Key

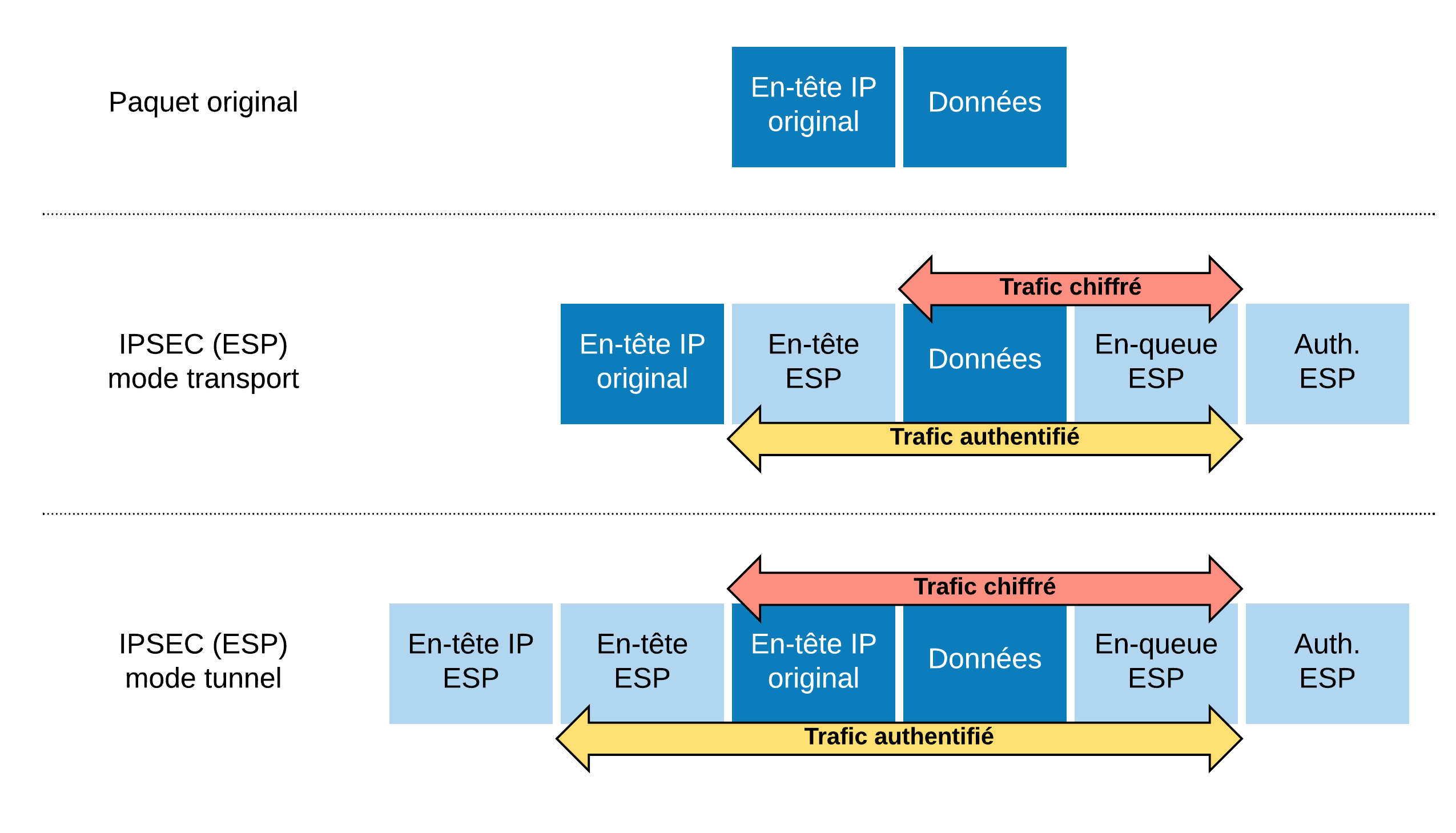
Methods For Implementing The Encapsulation Of Ipsec Header Download Scientific Diagram